What are Policies?
Policies are rules written in OPA Rego or Kyverno that validate your infrastructure before deployment. Each policy can either:- Deny - Block the build or deployment when a violation is detected
- Warn - Log a warning but allow the build or deployment to continue
- Build-time: Policies run during the component build process
- Deploy-time: Policies run after the plan is generated, before applying changes
- Sandbox runs: Policies run during sandbox infrastructure provisioning
Policy Types
Nuon supports policies for different component types, each with its own input format:| Type | Applies To | Engine | Evaluation Phase | Input Format |
|---|---|---|---|---|
container_image | External container images | OPA | Build | Image metadata (SBOM, signatures, attestations) |
helm_chart | Helm chart components | OPA | Deploy | Kubernetes AdmissionReview |
kubernetes_manifest | Kubernetes manifest components | OPA | Deploy | Kubernetes AdmissionReview |
terraform_module | Terraform module components | OPA | Deploy | Terraform JSON plan |
kubernetes_cluster | Kubernetes cluster resources | Kyverno | Deploy | Kubernetes resources |
sandbox | Sandbox infrastructure | OPA | Sandbox run | Terraform JSON plan |
Policy Engines
OPA (Open Policy Agent)
OPA policies are written in Rego, a declarative query language. Policies must be in thenuon package and use deny or warn rules.
The input structure varies by policy type:
| Policy Type | Input Structure |
|---|---|
terraform_module, sandbox | input.plan.resource_changes, input.plan.terraform_version |
helm_chart, kubernetes_manifest | input.review.object, input.review.kind |
container_image | input.image, input.tag, input.metadata |
Kyverno
Kyverno policies use YAML syntax and are designed for Kubernetes resources. Kyverno is only supported forkubernetes_cluster policy types:
How do you configure Policies?
Create apolicies.toml file at the root of your app directory. Policy content (Rego or Kyverno YAML) can be inline or referenced from files in a policies/ directory.
Directory Structure
Configuring policies.toml
Define policies in policies.toml with file references or inline content:
policies.toml
Policy Configuration Fields
| Field | Required | Description |
|---|---|---|
type | Yes | Policy type: container_image, helm_chart, kubernetes_manifest, terraform_module, kubernetes_cluster, or sandbox |
engine | No | Policy engine: opa or kyverno (default) |
name | No | Human-readable name. If not specified, derived from the filename |
components | Yes | List of component names this policy applies to. Use ["*"] for all components of the specified type |
contents | Yes | Inline policy content or path to policy file (e.g., ./require-encryption.rego) |
Referencing External Policy Files
Thecontents field supports multiple source types. Relative paths are resolved from the policies/ directory:
Syncing Policies
Policies are part of your app configuration. To create or update policies, sync your app: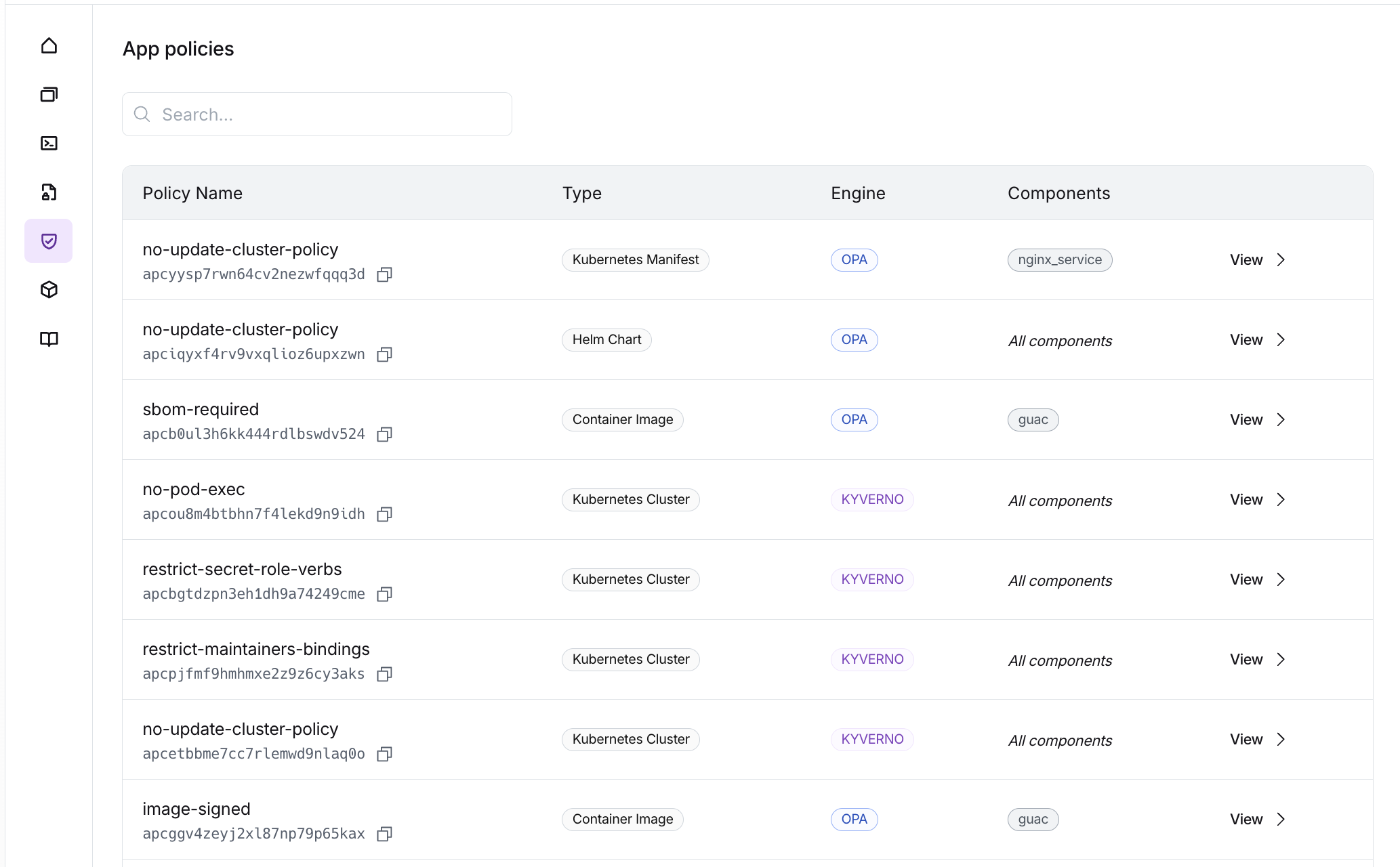
nuon apps sync again to upload the changes.
Note that unlike components, policies do not need to be built, they are evaluated directly during build and deploy workflows.
Policy Evaluation
Build-Time Evaluation
Build-time policies are evaluated during the component build process:container_image: Policies evaluate image metadata (SBOM, signatures, attestations) fetched from the registry
deny rule matches during build-time evaluation, the build fails with status policy_failed.
Deploy-Time Evaluation
Deploy-time policies are evaluated after the plan is generated, before applying changes:terraform_module: Policies evaluate the Terraform JSON planhelm_chart: Policies evaluate the Kubernetes AdmissionReview objectskubernetes_manifest: Policies evaluate the Kubernetes AdmissionReview objects
deny rule matches during deploy-time evaluation, the workflow step fails and changes are not applied.
Sandbox Evaluation
Sandbox policies (type = "sandbox") are evaluated during sandbox infrastructure runs. They receive the Terraform JSON plan for the sandbox infrastructure.
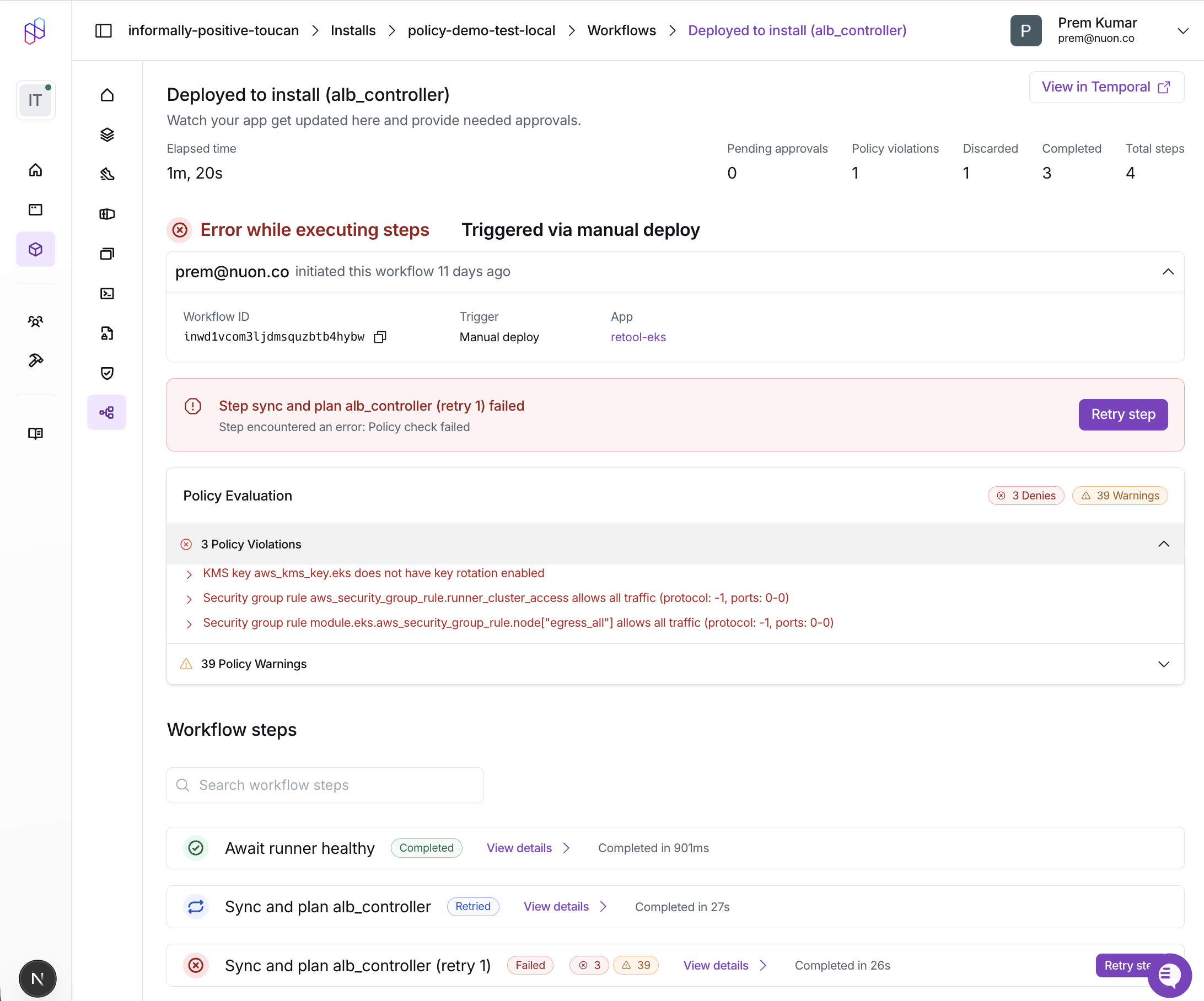
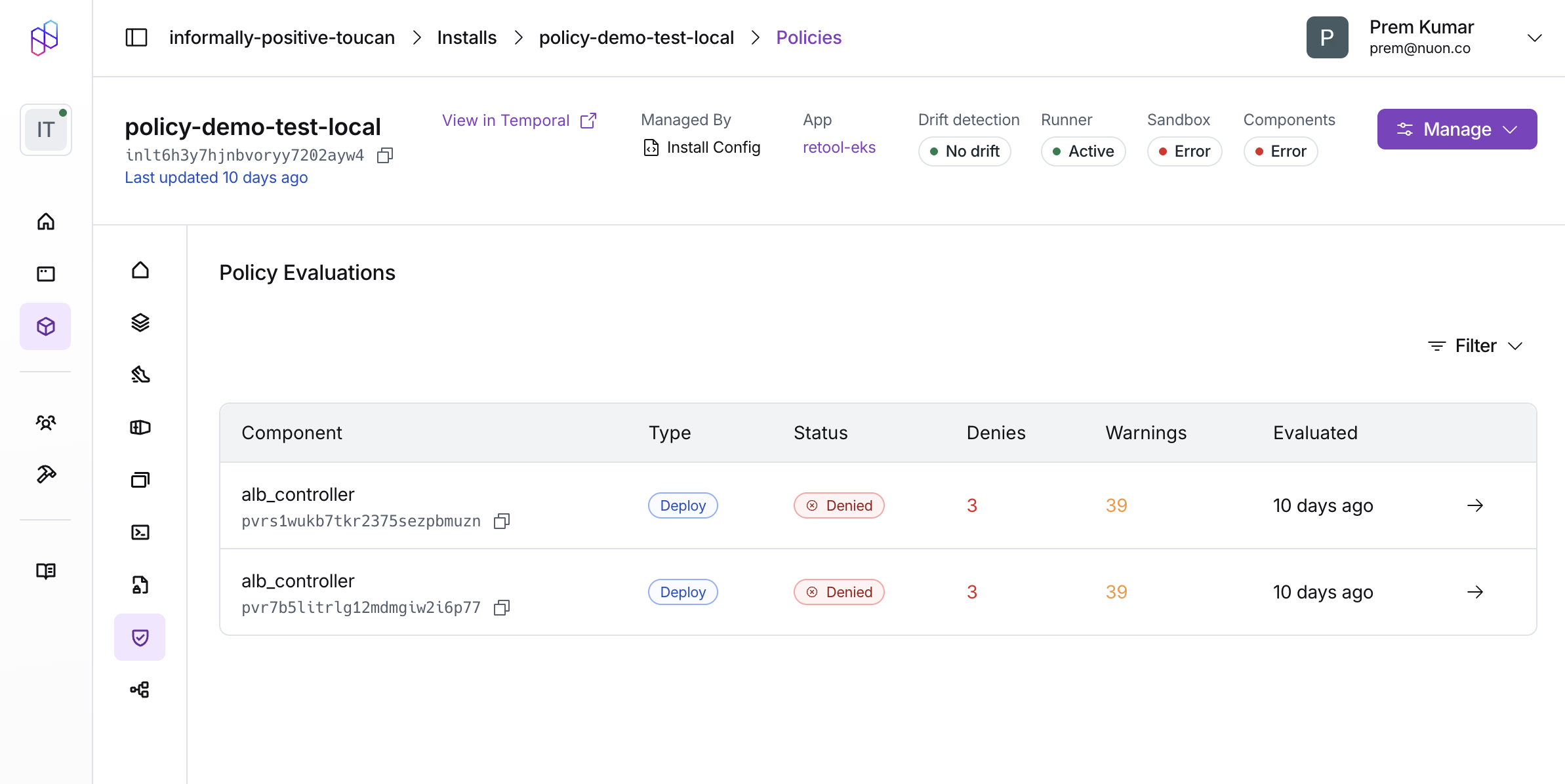
Viewing Policy Results
Dashboard
Policy violations are displayed in the workflow step details. The Policy Evaluation card shows:- Passed: All policy checks passed successfully
- Denies: Policy violations that blocked the workflow (red)
- Warnings: Policy warnings that were logged but didn’t block (orange)
deny or warn rule.
CLI
Build failures due to policy violations show thepolicy_failed status:
Policy Examples
We maintain a collection of example policies
organized by component type to help you get started.
terraform/- Policies for Terraform modules (encryption, tagging, IAM security, cost controls)kubernetes/- Policies for Helm charts and Kubernetes manifests (pod security, resource limits, networking)
Related Resources
- External Image Policies Guide - Detailed reference for container image metadata and Rego patterns
- Policy Configuration Reference - Schema reference for policy configuration
- Example Policies Repository - Ready-to-use policy examples