App Life Cycle
Package your app
The first step in the app life cycle is to package your app as a set of TOML files in a git-backed repository. These files define the app’s sandbox (e.g., VPC, networking, and Kubernetes infrastructure), components, inputs, variables, and other configuration details. These configurations can point to your existing Terraform modules, Helm charts, Kubernetes manifests, or other infrastructure-as-code resources. For examples of packaged apps, see our public GitHub repository. Packaging your app can be customized to re-use existing VPCs, networking, or Kubernetes clusters, or by default Nuon creates new ones for each install.Sync and Build
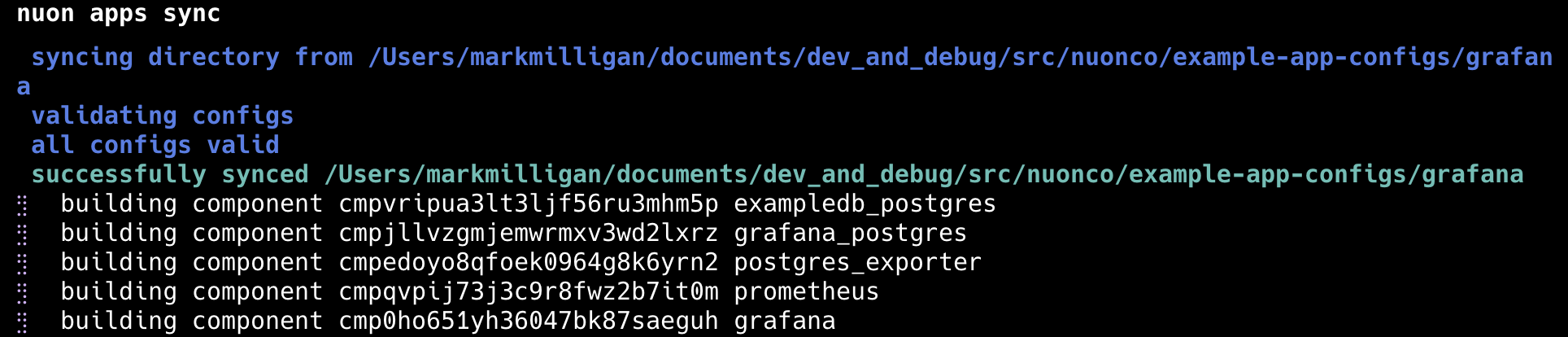
When an app is initially created and synced to the Nuon control plane with the Nuon CLI, a build occurs for each component in the app. Builds create an OCI artifact for each component and the Nuon control plane stores them in the container registry like AWS ECR. Important: After the initial sync, component changes require rebuilding.nuon apps sync will automatically rebuild when it detects changes to TOML files or referenced files like Helm values.
- Git repository source code changes (e.g., Terraform modules or Helm charts)
- Source code in your app repository changes (push your branch first, then rebuild)
nuon apps sync whenever anything in your TOML files changes.
Install Life Cycle
Installs, defined for your customers
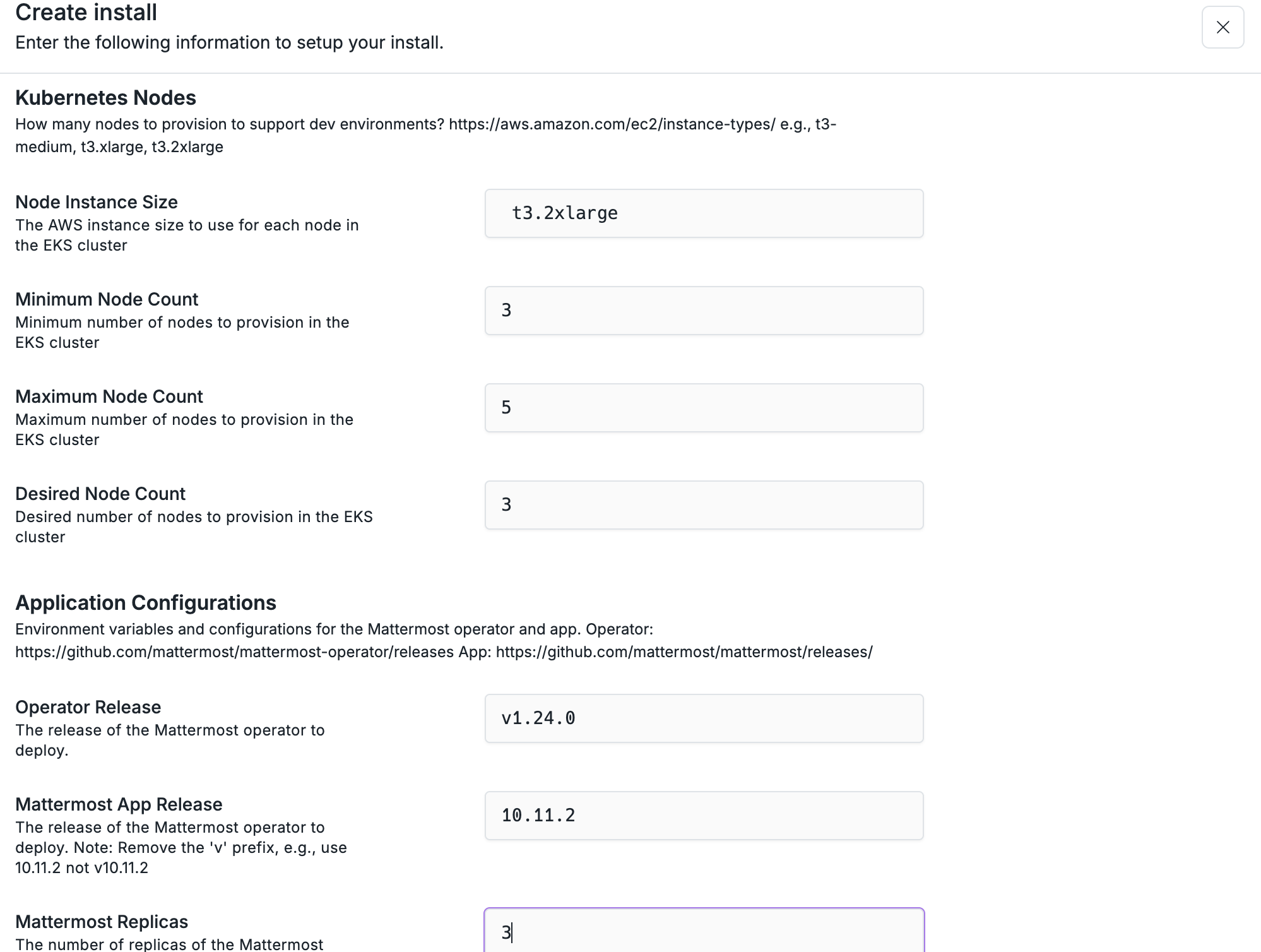
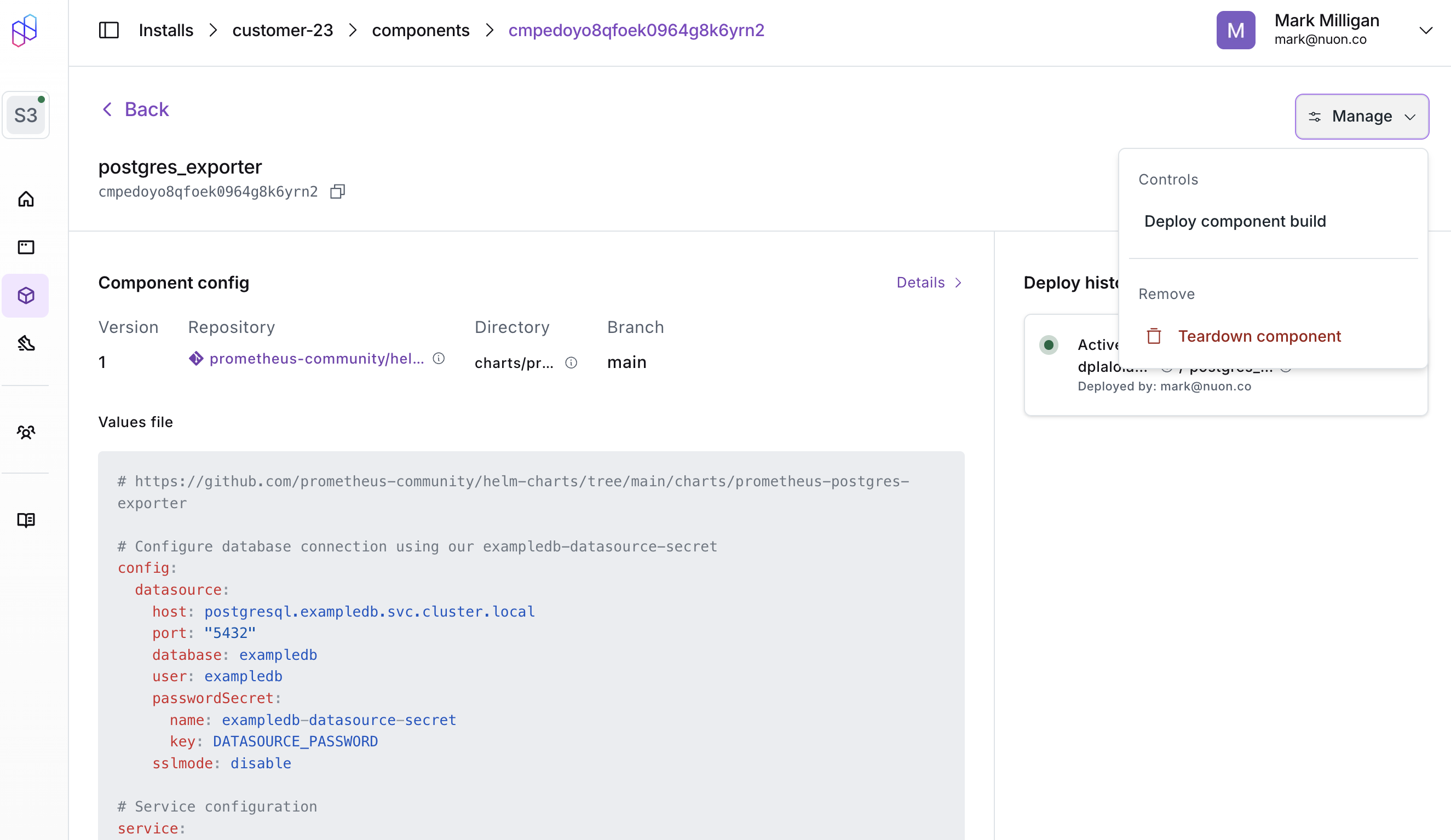
Installs into customer cloud accounts are created from apps and inherit the infrastructure and components defined in the app. When an install is created, it uses the latest built version of each component. An install’s life cycle is managed by workflows that define the steps to deploy, update, manage, and tear down the install.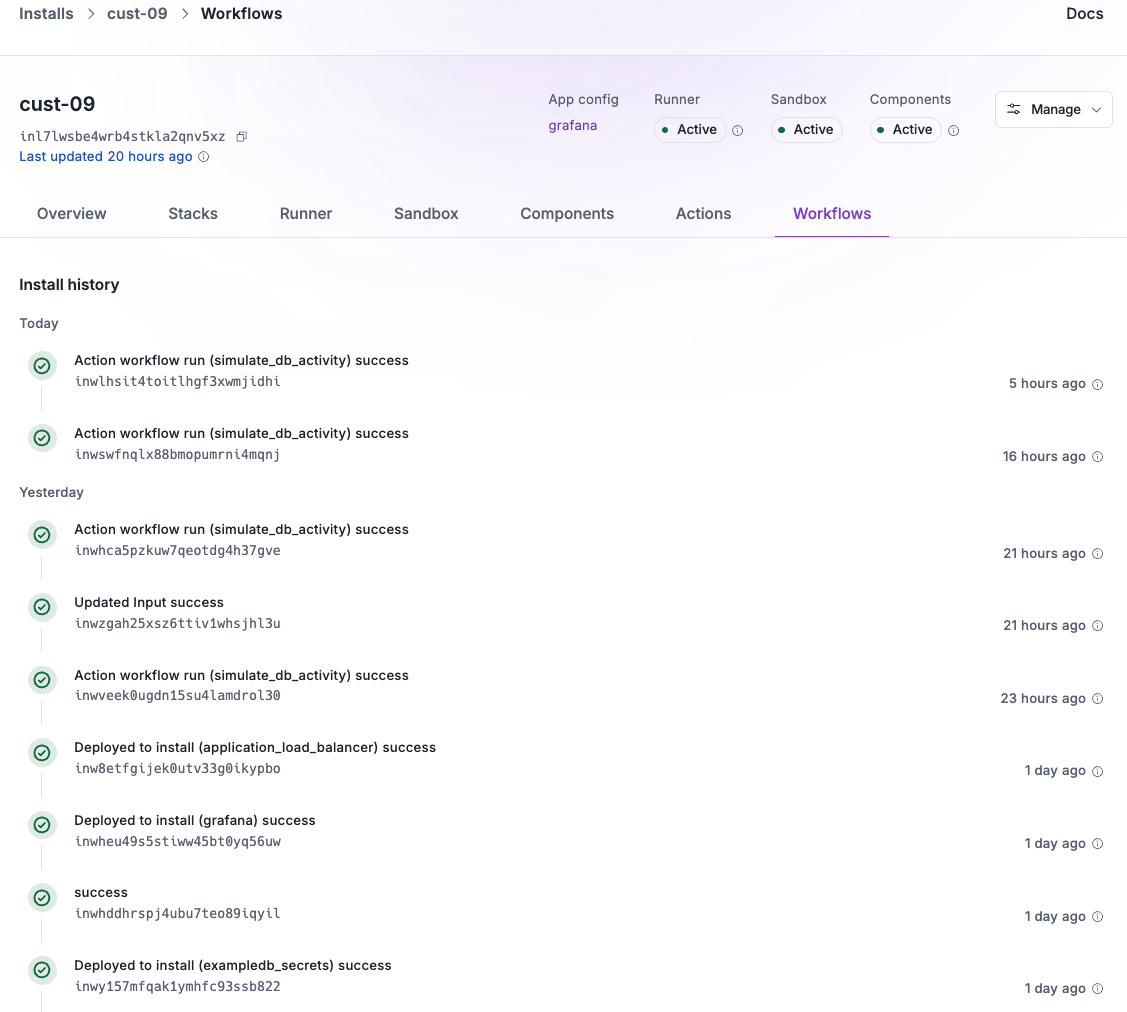
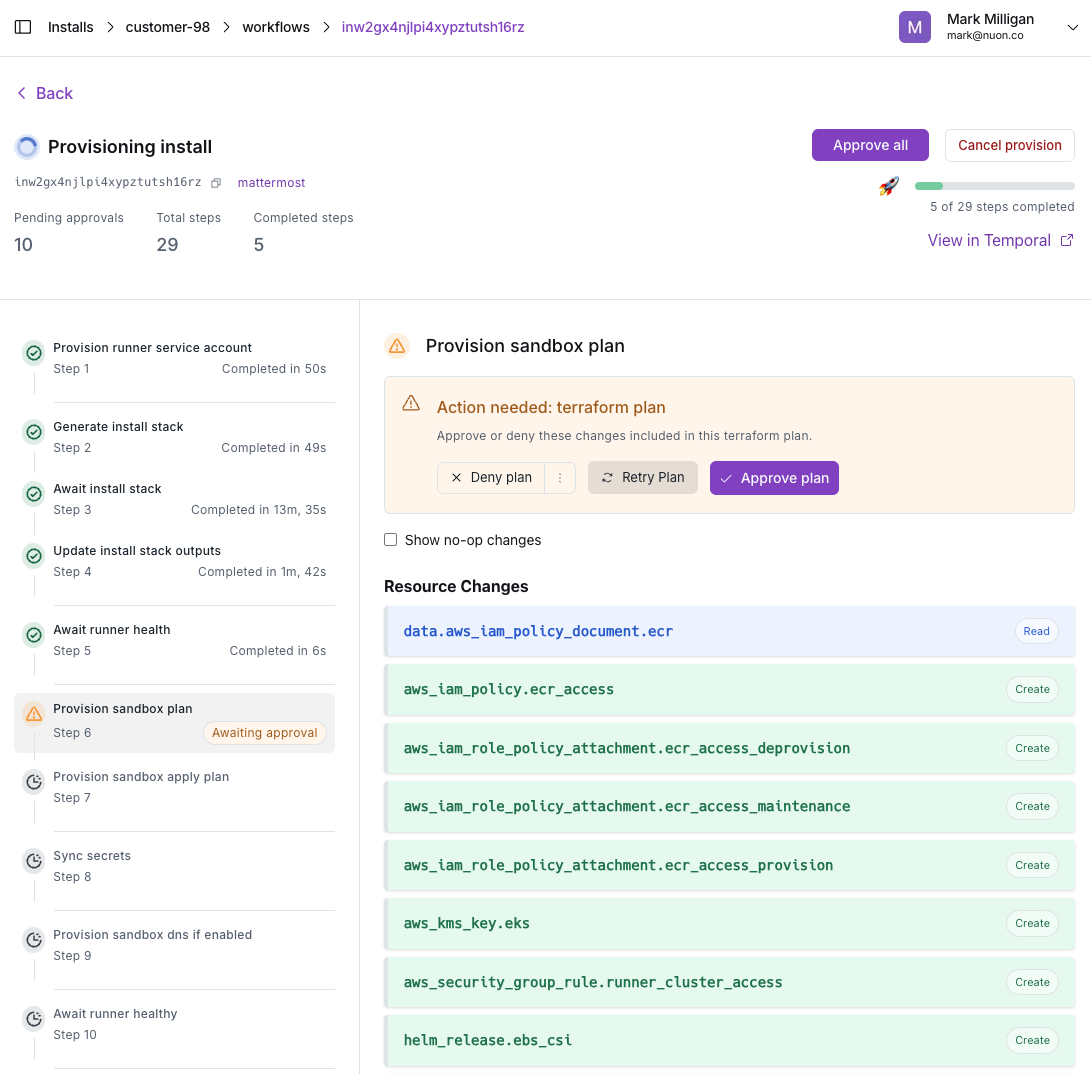
Update, with change controls
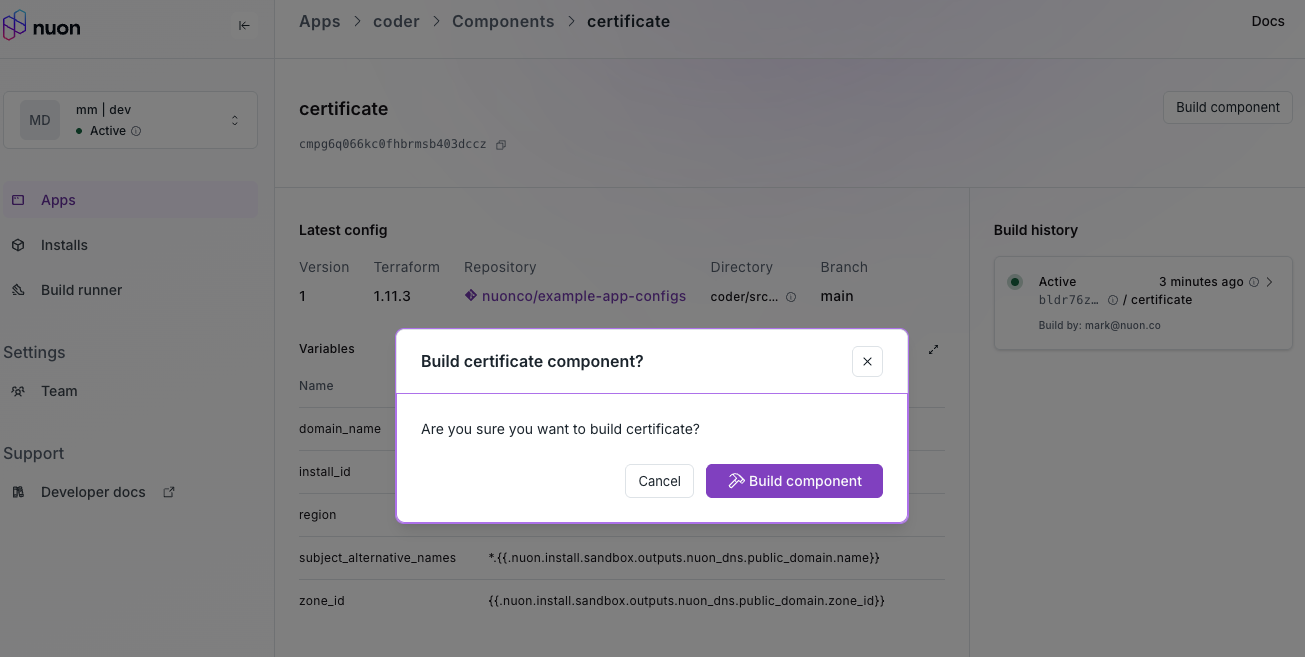
Because apps are git-backed, you can update individual or multiple installs to the latest release of your app or upgrade components or even infrastructure. e.g., Kubernetes version. Updates have approval gates by default to ensure changes are reviewed before being applied to customer installs. e.g., Helm diffs, Terraform plan outputs. The user can optionally Accept All approvals to streamline the update process.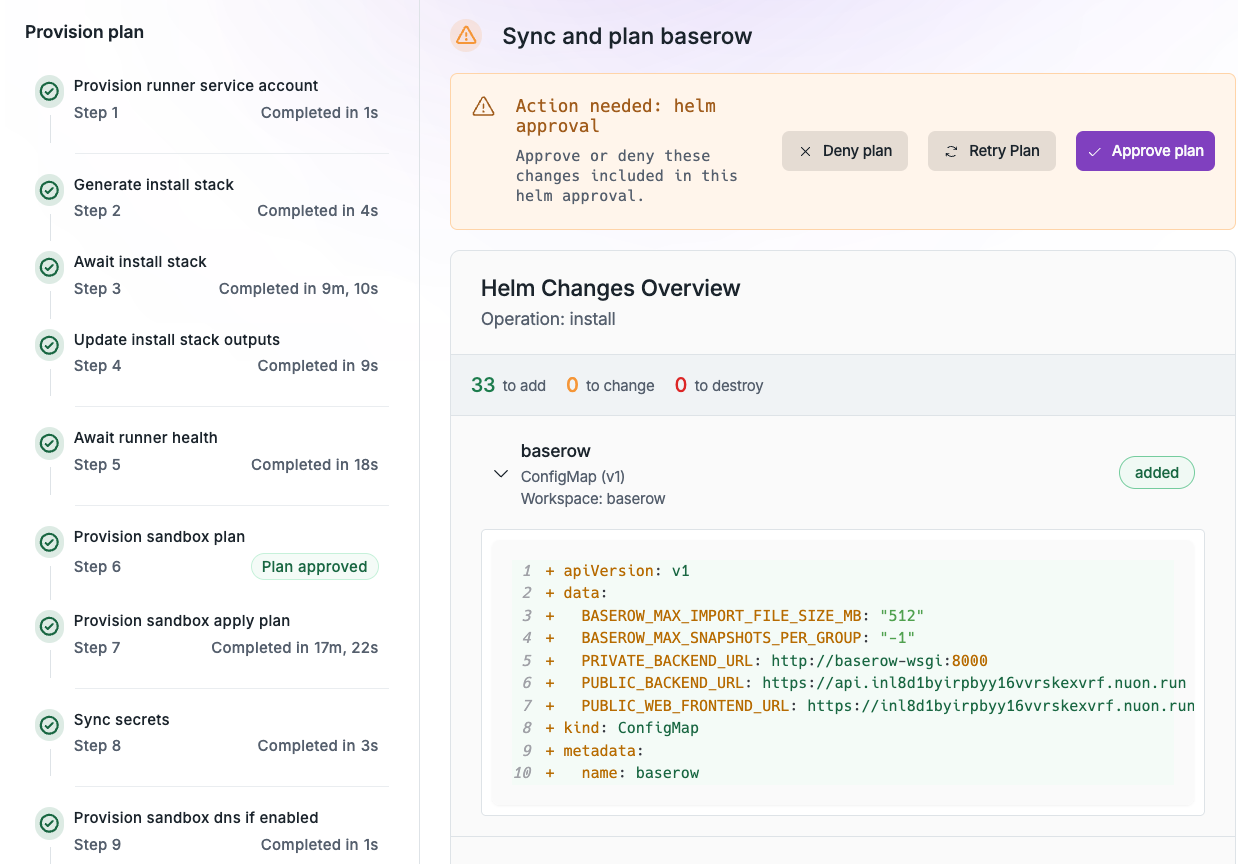
Monitor and Remediate
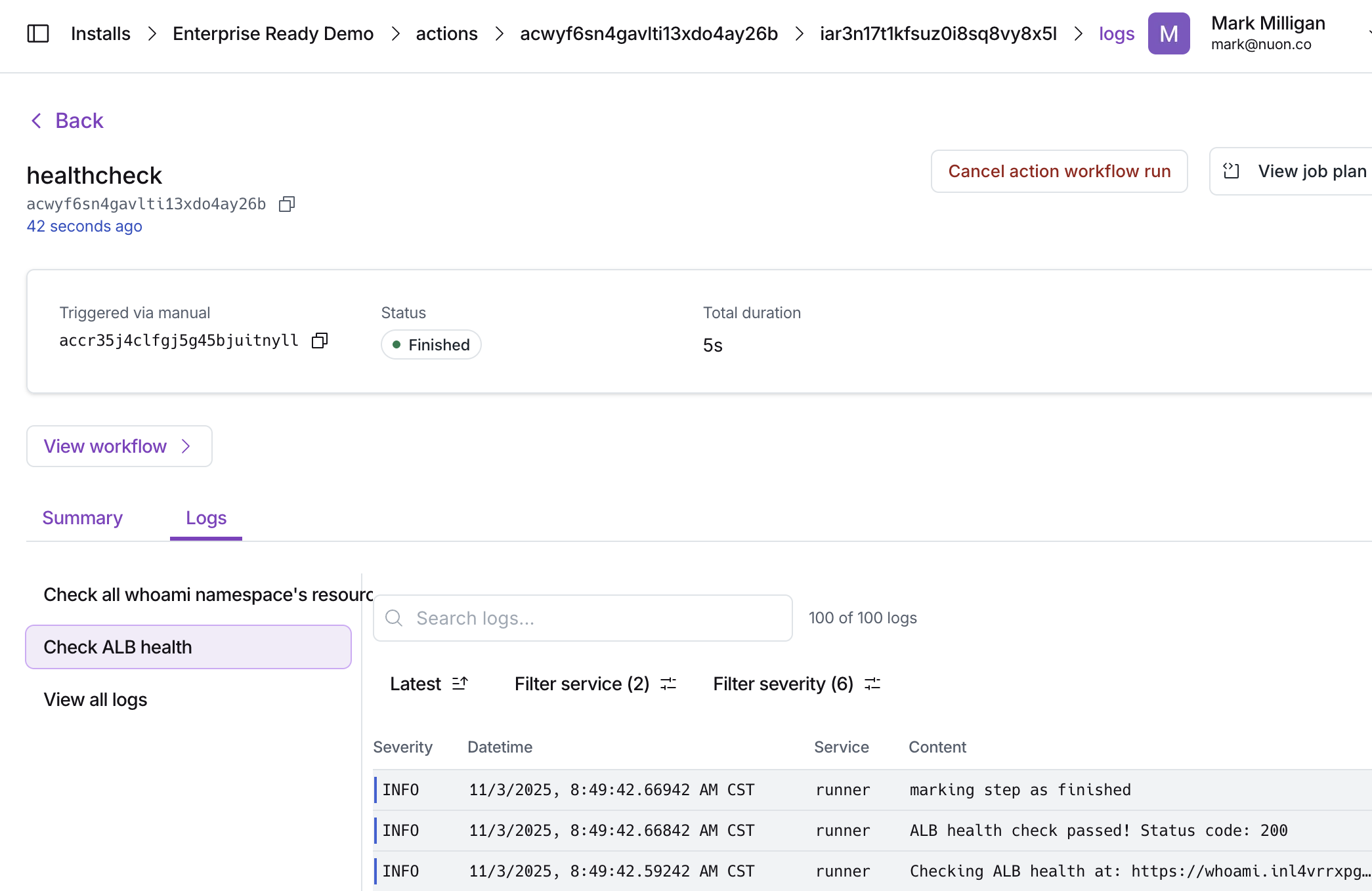
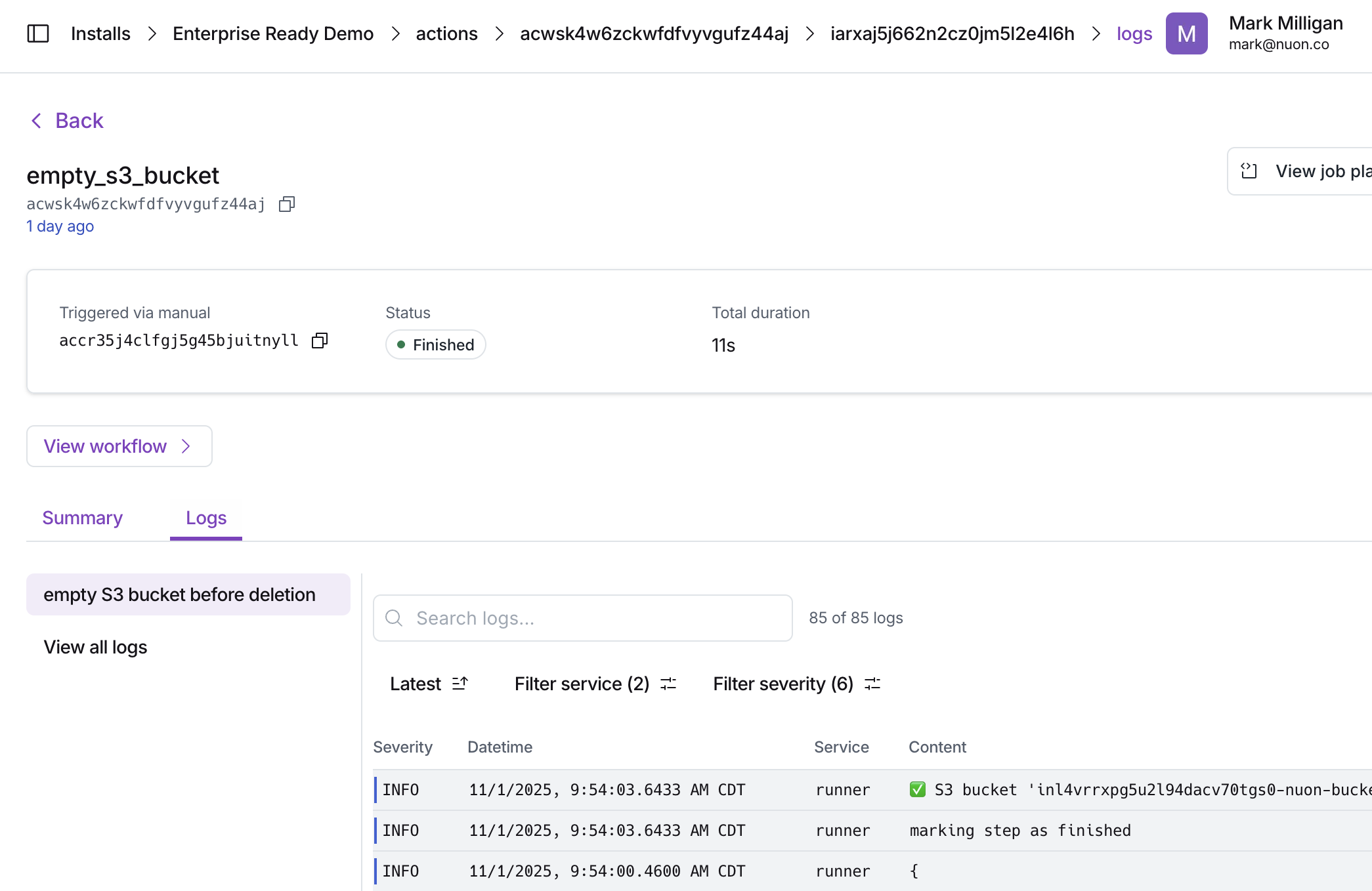
Once deployed, installs can be monitored for health and performance metrics with actions, bash scripts included in the app. e.g., checking pod status, disk space, ALB availability, etc.